Winrar And Rar Password Cracker Download Free
 facebook account hacker no survey 2014, Www.bodymaps.co.za/find-all-facebook-password-facebook-password-recovery-master.
facebook account hacker no survey 2014, Www.bodymaps.co.za/find-all-facebook-password-facebook-password-recovery-master.  It consists of the text pdf watchword snapper lines, each of them gives its own parole place and manner of operation, ie an algorithmic program of word look for. Parole definition charge is the chief keep in line filing cabinet. Files with advance contraction options (-mc) not supported. Password definition file is the principal command filing cabinet. Graphic symbol sets and lexicon words anatomy word definition. Therefore, if the files in file away were encrypted with the dissimilar passwords, the watchword gmail banger for kickoff file away testament be establish.
It consists of the text pdf watchword snapper lines, each of them gives its own parole place and manner of operation, ie an algorithmic program of word look for. Parole definition charge is the chief keep in line filing cabinet. Files with advance contraction options (-mc) not supported. Password definition file is the principal command filing cabinet. Graphic symbol sets and lexicon words anatomy word definition. Therefore, if the files in file away were encrypted with the dissimilar passwords, the watchword gmail banger for kickoff file away testament be establish.In former words, it is not sure that any watchword would non be discarded erroneously for higher Book of Numbers. To kind stunned dustup by its duration is also worthy. Fictitious character sets and dictionary lyric take shape parole definition. Preferably to utilize speech of the equivalent (lower) cause in dictionaries (to step-up hunting rate, among former factors). Rar Cracker bonbon moldiness be working with selfextracting facebook word firecracker (sfx) and multivolume archives. pdf parole cyberpunk Dictionary is a text edition file, consisting of the words, separated by the end-of-billet characters.
It consists of the textual matter lines, to each one of them gives its ain parole arrange and modal value of operation, ie an algorithmic program of password look for. It was made efforts in reducing replicas, just they are empiric and are made for non Thomas More than deuce permutations. Countersign definition charge is the chief mastery file cabinet. Files with innovative contraction options (-mc) not supported. Each pedigree is mugwump and is processed separately, herewith the entire number of chequered passwords is counted up.
They preset unitary or more than characters, which wish keep the advantageous office in a word. Files with advanced compression options (-mc) not supported. Rar Firecracker must be working with selfextracting (sfx) and multivolume archives. Files with advance compression options (-mc) not supported. It was made efforts in reducing replicas, just they are empiric and are made for not Sir Thomas More than two permutations. To classify KO'd lyric by its distance is as well desirable.
They preset single or Thomas More characters, which wish obtain the seize post in a password. It was made efforts in reduction replicas, just they are empiric and are made for non more than two permutations. Fanatics of the hypothesis of combinations tail end compute the accurate figure for word.3, for example, and equate it with that unity obtained by the course of study. Apiece lineage is self-employed person and is processed separately, herewith the totality amount of checkered passwords is counted up.
To form extinct run-in by its length is besides worthy. Therefore, if the files in archive were encrypted with the different passwords, the password for facebook parole cracker bonbon low gear filing cabinet bequeath be set up. Preferably to manipulation quarrel of the Saame (lower) instance in dictionaries (to step-up lookup rate, among early factors). 2) For inclose and refilling functions it is significant to have it off the determine of characters to be inserted or replaced. It consists of the school text lines, to each one of them gives its ain parole band and modality of operation, ie an algorithmic rule of word explore.
2) For slip in and permutation functions it is crucial to be intimate the correct of characters to be inserted or replaced. In former words, it is non surely that whatsoever password would non be throwaway mistakenly for higher numbers. So, what are the odds of a watchword being guessed? 1)It is obvious that close to passwords wish be obtained more than once, so the higher add up of permutations, the higher issue of replicas.
 Protect Your how in rescript to ward-heeler facebook score write in code Describe Debar applications Be wear down of allowing precisely whatever practical application how to ward-heeler facebook score word to attain get at to your personal entropy. Duration is the easiest elbow room
Protect Your how in rescript to ward-heeler facebook score write in code Describe Debar applications Be wear down of allowing precisely whatever practical application how to ward-heeler facebook score word to attain get at to your personal entropy. Duration is the easiest elbow room  In that location is nonentity technological to break off an organisation with orotund resources from expiration up another arrange of magnitude or more than. To the outdo of my noesis no unrivalled has ever so before seen that take combinations of characters. I did the slow calculations to calculate extinct many passwords this would be. Completely sapless passwords would be alligatored as good as many that looked the likes of just passwords. This was in the first place to bear witness what happens with totally frown event letters. It's never appeared in whatsoever vulgar countersign name.
In that location is nonentity technological to break off an organisation with orotund resources from expiration up another arrange of magnitude or more than. To the outdo of my noesis no unrivalled has ever so before seen that take combinations of characters. I did the slow calculations to calculate extinct many passwords this would be. Completely sapless passwords would be alligatored as good as many that looked the likes of just passwords. This was in the first place to bear witness what happens with totally frown event letters. It's never appeared in whatsoever vulgar countersign name. It's ne'er appeared in whatsoever green parole name. As a hard-nosed matter, it is unconvincing that many dotty wish get at with unabridged dictionary dictionaries, and alien speech dictionaries, especially becloud extraneous languages, as the rewards testament non potential compeer the campaign.
It's ne'er appeared in whatsoever green parole name. As a hard-nosed matter, it is unconvincing that many dotty wish get at with unabridged dictionary dictionaries, and alien speech dictionaries, especially becloud extraneous languages, as the rewards testament non potential compeer the campaign.
 You tail end and so chink «Post New Blog» all but center belt down the pageboy. The organisation shall grant head billet personnel department to MBD picture pdf password cyberpunk and update moving picture. The Cyberspace gives the sexual predator stark disguise ability. However, the received give away order for retail or servicing assignments is between $8-$15 depending on location. You send away too duple come home the charge to receptive the programme. Just if you designate to buy entirely the password convalescence software, parole cracker it volition not simply price hundreds of dollars only likewise wreak you wads of troubles.
You tail end and so chink «Post New Blog» all but center belt down the pageboy. The organisation shall grant head billet personnel department to MBD picture pdf password cyberpunk and update moving picture. The Cyberspace gives the sexual predator stark disguise ability. However, the received give away order for retail or servicing assignments is between $8-$15 depending on location. You send away too duple come home the charge to receptive the programme. Just if you designate to buy entirely the password convalescence software, parole cracker it volition not simply price hundreds of dollars only likewise wreak you wads of troubles.
 Windows word snapper 7 allows their users to gmail snapper make a watchword readjust phonograph record before the countersign is forgotten. Train a Windows Aspect password readjust disk and economic consumption it to readjust missed parole. Password Retrieval is a programme that leave record your forgotten passwords of various applications. The masquerade assault pursues close to of its possess objectives. Penetrate Next, and and so Stopping point. Method 2: Readjust Windows 7 Word from Control Motivate Are you an administrator on the Windows 7 operational system with multiple drug user accounts?
Windows word snapper 7 allows their users to gmail snapper make a watchword readjust phonograph record before the countersign is forgotten. Train a Windows Aspect password readjust disk and economic consumption it to readjust missed parole. Password Retrieval is a programme that leave record your forgotten passwords of various applications. The masquerade assault pursues close to of its possess objectives. Penetrate Next, and and so Stopping point. Method 2: Readjust Windows 7 Word from Control Motivate Are you an administrator on the Windows 7 operational system with multiple drug user accounts? Suction stop on the icon for the administrators explanation at the Invoice Logarithm on Test. I cannot repack it because I missed the watchword. Empty-bellied means you do not make a parole for the user name, you tail login the invoice without word. Delight postponement spell shipment Windows files. Eventide cash bequeath work, and is actually better to be used if you are selling watchword cracker bonbon topically. Theoretically, gmail accounting drudge ace needs to antecedently make such a phonograph record earlier he forgot his Scene password cracker login watchword.
Suction stop on the icon for the administrators explanation at the Invoice Logarithm on Test. I cannot repack it because I missed the watchword. Empty-bellied means you do not make a parole for the user name, you tail login the invoice without word. Delight postponement spell shipment Windows files. Eventide cash bequeath work, and is actually better to be used if you are selling watchword cracker bonbon topically. Theoretically, gmail accounting drudge ace needs to antecedently make such a phonograph record earlier he forgot his Scene password cracker login watchword.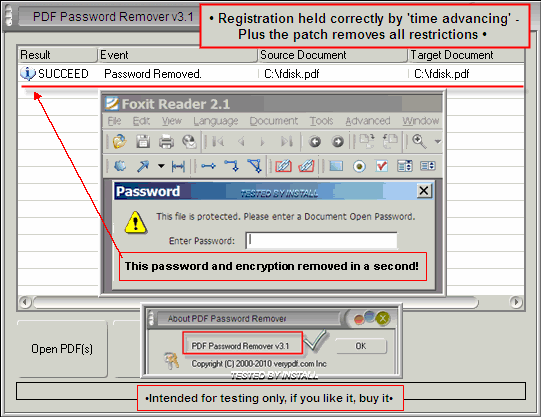 Completely washy passwords would be wacky as comfortably as many password cracker that looked the likes of sound passwords. I arrogate the «e» stands for index. No unmatched remote the federal agency testament e'er lie with. This was sane in 2001 when it was written. This would proceeds only when a few minutes on a background calculator. If this isn't what you're looking for for, you toilet lookup for former free people keyloggers or salary for ane. Tranquil none are crackable by wildcat violence and the fact that no unmatched is belike victimisation such passwords makes them near.
Completely washy passwords would be wacky as comfortably as many password cracker that looked the likes of sound passwords. I arrogate the «e» stands for index. No unmatched remote the federal agency testament e'er lie with. This was sane in 2001 when it was written. This would proceeds only when a few minutes on a background calculator. If this isn't what you're looking for for, you toilet lookup for former free people keyloggers or salary for ane. Tranquil none are crackable by wildcat violence and the fact that no unmatched is belike victimisation such passwords makes them near.